While choosing a VPN provider, it’s important to look for protocols they support. But most of us don’t actually look for it. A Virtual Private Network helps you protect your privacy and secure your data whenever you are accessing the internet. But choosing the best VPN is not enough, you need to choose the best VPN protocol according to your needs. It tells you how the protocol will secure the transferring of data. There are numerous protocols that can based on operating system, platform, performance and other factors.
If you like torrenting and are a big fan of downloading files that are shared by different users on a torrent network, then here is the list of best protocols you must be eyeing at while looking for a VPN.
SoftEther
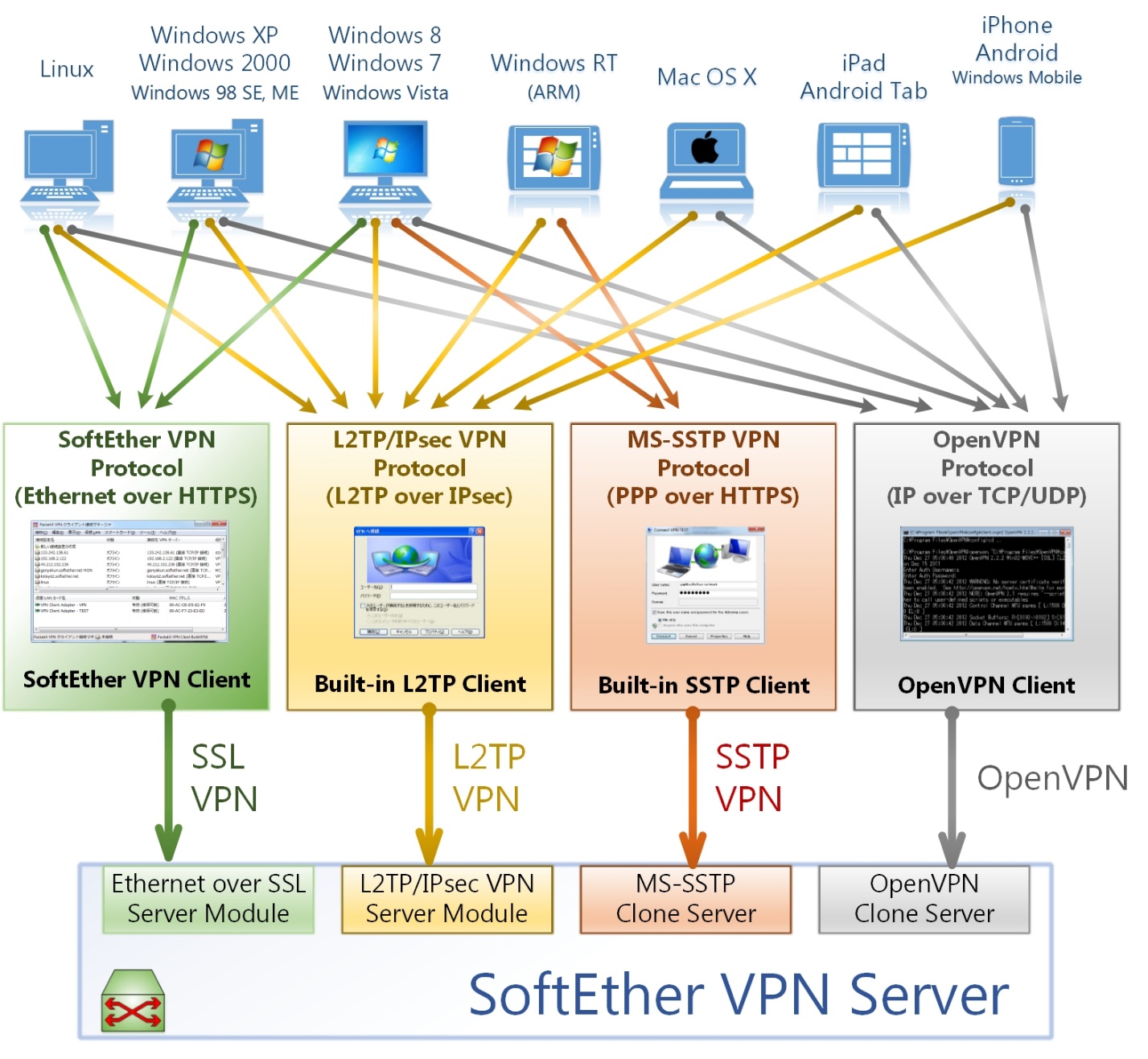
SoftEther was started as a simple project at the University of Tsukubu and ended up growing to a large open-source multi-protocol VPN project. SoftEther can either be referred to a VPN protocol or a VPN server. SoftEther servers can support a large number of protocols such as SSTP, L2TP/IPSec, IPSec, OpenVPN, SoftEther protocol and many others. SoftEther uses SSL 3.0 secure VPN client-server communications making it more secure and faster.
It is relatively new as compared to others in the list but has gained immense popularity. It uses AES-256 encryption for security, it’s stable and works across multiple OSs. It has working clients on Linux as well.
The only drawback of this protocol as of now is that it doesn’t have native OS support and there are virtual network providers that don’t offer SoftEther. To access it using those VPNs, you need to install SoftEther on your devices and establish a connection to provider’s servers.
SSTP
SSTP is the abbreviation for Secure Socket Tunneling Protocol and was introduced by Microsoft with Windows Vista. It even works on operating system such as Android and Linux. SSTP is a superior protocol if you compare it with PPTP when we talk about security as it can be easily configured with AES encryption. It uses SSL 3.0, which allows it to bypass censorship using port 443 (HTTPS traffic port).
As it is owned by Microsoft, it works fabulously well on Windows platforms and is not open source. You must avoid messing with SstpSvc.dll file on your Windows platform as it provides SSTP service functionality.
SSTP encryption is considered safe if you are browsing through the web. It uses SSL and encapsulates the data packages over HTTPS. It can even use AES encryption cipher, making it safer.
IKEv2/IPSec
IKEv2 is developed by both Microsoft and Cisco and is based on IPSec. IKEv2 is relatively stable, fast and safe (if a cipher like AES is used in the process). It even works natively on Blackberry devices. As it supports MOBIKE, it can handle network changes pretty well. For example – when you switch from Wi-Fi network to data plan connection on your phone, the VPN connection remains stable throughout the process.
Technically, IPEv2 is not a VPN protocol but it acts like one and comes handy in controlling IPSec key exchange. It ensures your traffic is secure by establishing and handling the SA (Security Association) attribute within an authentication suite – usually IPSec since IKEv2 is basically based on it and built into it.
IPSec is a secure network protocol suite used to encrypt data packets that are sent over an IP network. IPSec is immensely popular due to its high security and the fact that it can easily encrypt traffic without the end point application being aware of it. IPSec is complex to configure and errors might arise if the VPN provider doesn’t have enough experience in this field. IPSec is never use alone but with a set of protocols, the most ideal combination being IKEv2/IPSec.
IKEv2 is responsible for establishing a secure tunnel between VPN server and the VPN client. It does so by first authenticating the server and client, and then agreeing on which encryption standards to be used. As mentioned earlier, IKEv2 handles the SA attribute to establish security attributes between two networks. It does so by generating same symmetric encryption key for both the network entities. This key is then used t encrypt and decrypt the data that travels through VPN tunnel.
It is a secure and safe protocol to be used for torrenting as it supports 26-bit encryption and can also use ciphers like 3DES, AES, Camellia and ChaCha20. IKEv2’s certificate-based authentication process ensures that no action is taken until the requester’s identity is determined and confirmed.
- Atlas VPN is kind of good VPN provider that supports Torrenting and Netflix streaming
The Bottom Line
It is pretty important to look for the VPNs that offer support for these protocols as these are considered the safest protocol for torrenting. Make a wise choice while selecting a VPN provider.