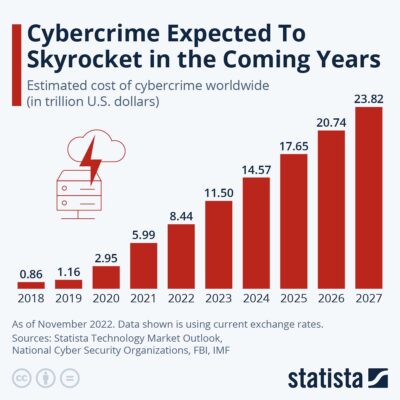
Ever stopped to wonder how companies manage employee activities and restrict certain things online for them? Or how some people bypass regional content blocks like it’s nothing? It’s not magic, it’s proxies. Proxy servers, to be precise. These intermediary servers slip between you and the wider web, doing more than just rerouting traffic. They can
SSL Proxies: Secure Routing with SSL Proxies
SSL proxies play a central role in online privacy and encrypted traffic routing. These proxies operate by intercepting HTTPS traffic and forwarding it securely using SSL (Secure Sockets Layer) encryption protocols. The key benefit of SSL proxies is that they allow users and organizations to browse, scrape, or audit web content over secure HTTPS connections
14 Best Mobile Proxy Services For All Kind Of Users In 2025
Proxies are the unseen hands that pull the strings in the huge, always-changing digital universe, protecting identities, collecting information, and providing access to otherwise forbidden areas. However, proxies are not all made equal. Some stand tall as pillars of dependability and scale, while others are designed for speed or stealth. The correct proxy provider is
14 Best Proxy Server Software| We Liked 1st One
Businesses looking for improved security and anonymity require a trustworthy proxy server. Geo-restricted content can be unlocked, site scraping effectiveness can be increased, and online privacy can be protected with the correct proxy service. The top 14 proxy server software options are highlighted in this guide. They were chosen with care based on factors including
Reliable UK Proxies: Where to Find Free and Paid Options
Proxy servers have become essential tools for maintaining privacy and accessing geo-specific content across the web. UK proxies, in particular, allow users worldwide to adopt a United Kingdom IP address, bypassing region-based restrictions for various services, secure browsing, and enhanced online privacy. But when it comes to choosing proxies, deciding between free and paid options
What Is Security Awareness Training and Why Is It Important?
As time goes on, cyber threats are becoming more sophisticated and increasingly pervasive. So, the significance of security awareness training cannot be overstressed. Despite possessing a foundational understanding of cybersecurity, many professionals may overlook the crucial role that awareness and behavioral change play in fortifying an organization’s defenses. This guide aims to dissect the concept
How to Create and Set up Google Passkeys 2025
Passkeys are undoubtedly a better version of signing into a website. It is a great alternative to passwords as you have to remember your password whenever you sign in. With Passkeys, OTP can also become irrelevant to some extent. Passkeys are the new standard with proper protocols backed up by Google itself. This guide shows
Veracrypt vs Bitlocker Which is the Best One For Windows 11 10
Encrypting your files is the ultimate form of securing and keeping the files safe from cyber thieves. Several forms of encryption gets the job done for many people. However, research shows that the best encryption method is to encrypt the whole disk or create an encrypted container. While there are many options available on the
Best Keystroke Encryption Software for Windows 11 Laptop PC Desktop
Knowing that someone could be recording what keys you are pressing can be scary. They can get information about all your passwords and credentials using keyloggers. Below are the best keystroke encryption software to prevent cyber threats from stealing your information. Best Keystroke Encryption Software Zemana AntiLogger Zemana AntiLogger is a powerful and easy-to-use program
The Ultimate Guide to Creating a Cybersecurity Strategy for Your Business
As the digital landscape progresses, businesses also encounter evolving cyber threats. In this interconnected world, a robust cybersecurity strategy is not merely an option, but a necessity for any business, irrespective of its size or industry. This guide aims to provide you with comprehensive insights into creating a cybersecurity strategy for your business, covering everything
Navigating the Digital World: How Proxies Drive Anonymity and Privacy in the Age of Technology
The internet is fun and useful, no doubt. However, everything you do online leaves a digital footprint. Anyone anywhere can see your activities online. That sounds a bit creepy but it is what it is. This vulnerability has exposed many individuals and businesses to cyber threats like malware, Denial-ofService (DoS), phishing and SQL injection. Unfortunately,
Top 5 Cyber Awareness Challenges in 2025: A Detailed Guide
Since the beginning of 2023, small-scale businesses and giant corporations have suffered from various cybersecurity threats. And with elements like AI, cloud services, and cryptocurrency introduced into the mix, the challenges get more complicated. Here is a list of the top five cyber awareness challenges dominating the cybersecurity realm. Let’s get right to it: Cybersecurity
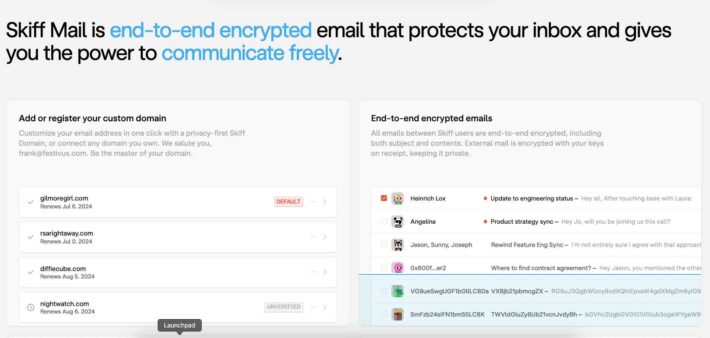
Skiff vs ProtonMail Which Is Secure And Better One For Emailing?
Mainstream email service providers have broken the user’s privacy. Many lawsuits have been filed in courts for peeking into the emails. ProtonMail and Skiff Mail have come forward with the solution for businesses and individuals. You can maintain the privacy of the email contents of everyone. And we have a clear winner in the comparison.
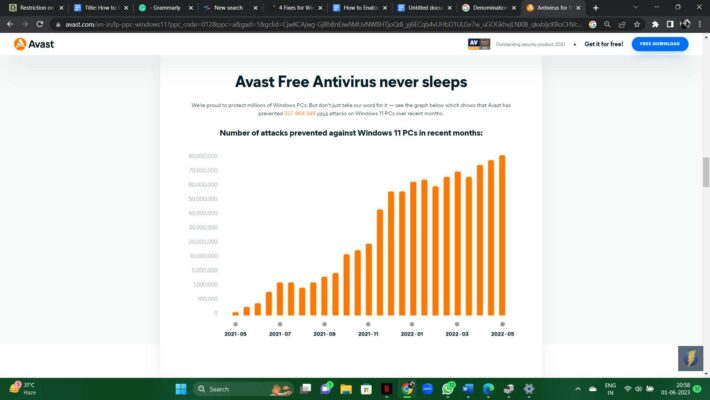
Avast Antivirus Offline Installer Download 2025 FREE PRO 64 Bit
In the rapidly advancing digital era, protecting your computer and personal information from cyber threats is of utmost importance. Avast Antivirus stands as an exceptional security solution, offering an array of features meticulously designed to shield your devices from viruses, malware, and other online dangers. In this comprehensive review, we delve into the depths of
How Indonesian Proxy IPs Can Help You Access Blocked Websites
Most people have spent their time using the Internet for different purposes. Internet connectivity and online sources have become essential in today’s digital environment. However, some services and websites may be limited due to government censorship or geographical considerations. Fortunately, using proxies can help you access blocked websites. This article will outline how proxies like
9 Best Windows 11 Antivirus 2025 [FREE] PC, Laptop, Surface Pro, Desktop
We all know the basic use of Antivirus software i.e. to protect our computer system from viruses and malware. If you are using Windows 11 and searching for a reliable Antivirus app, then here’s the list of the 9 Best Free Windows 11 Antivirus software for you. The list contains the top-rated and free-to-use Antivirus
The Best Encryption Software For MacOS 2025, Macbook Air, Pro, M2, M1, Studio, iMac
Even if you have already installed anti-virus software on your Mac, your Mac system is still not 100% safe. There are still some chances of losing your data to hackers as hackers are quite active and use advanced technology tools to hack your PC systems. For that reason, you must use encryption software on a
5 Key Strategies for Preventing Cyber Attacks in 2025
Cybersecurity as a topic starts to take place in high-level meetings. This means one thing; businesses are getting more concerned with global cybersecurity threats. And for good reasons, as this Cyber Security Analysis report shows us, different industries are being targeted by hackers. If you’re unfamiliar with data breaches and their impact on businesses, it’s
Security Compliance Explained Briefly: What Is It?
We all know what compliance means in business; it is when an organization abides by the regulations or the standards set by authorities in a particular area. These can be related to industrial safety, privacy, or as we will talk about; security compliance. Security compliance in web-based businesses is relatively a new concept. Since we
Apple vs Android security
iOS and Android are two of the most popular mobile operating systems in the world. The Android market share is larger, but iOS is more profitable. Both have their pros and cons in the security department. iOS has a reputation for being more secure than Android. This is because Apple has complete control over the