A cyber attack is an attack done deliberately from one or more computers against another computer, multiple computers or networks. The goal is to breach the information system of another individual or organization. The organizations all over the globe today face the major challenge of protecting their businesses from the cybercrime.

The worldwide cybercrime damages in 2015 amounted to a massive $3 trillion and the forecasts mention that the amount will be doubled in 2020. To protect yourself from cyber attacks first you need to know about the different types of attacks. Then with that knowledge in mind you can take steps to secure your network.
Contents
COMMON TYPES OF CYBER ATTACKS
There are different forms of cyber attacks depending on the target. The hackers target the security holes created by people due to negligence, employee turnover or human error. Many times the security holes are in the networks themselves.
Password Cracking Attacks

The attack is forced through the password-cracking software. The password rules have made passwords less secure. Always use random and long passwords which are more difficult for machines to guess. Use different passwords for business and personal uses and change them on a regular basis. You can also use a password or credential manager.
Social Engineering Attacks
Password phishing emails are the most common types of social engineering attacks. The hackers spoof the emails sent out by companies like PayPal and Amazon. The aim is that the potential victims will follow the links in the email and enter their passwords or banking information.

The businesses should train and educate their employees to be vigilant while clicking email links before they enter their secure data. Two-factor authentication (2FA), a secure login system that requires a physical object as well as the username and password can be implemented. Example of 2FA- SMS you receive on a registered number or biometric data. Phishing detection tools such as email filters, anti-virus software, and firewalls give warning if they detect something suspicious.
Social Media Attacks
There are numerous fake profiles on Facebook. Often you get a friend requests or invitations to play a game. When you accept them the hackers get access to your profile which they take advantage of.

In companies, there is a team managing the company’s social media accounts. So they are more open to corporate hackers who can take over the account in order to embarrass the company. The employees should be instructed not to share the passwords for social media accounts. The social media managers should know what to look for to determine if an account has been hijacked. You can even train your Social Media manager with some basic cyber security trainings which will help you save your business from all the cyber threats. There are many companies providing training for the same. One such company is Alpine Security where you can get yourself trained on Cybersecurity, Penetration Testing, etc.
Malware Attacks

Malware refers to ‘malicious software’ which destroys or encrypts the files. The viruses, worms, Trojan horses act as malwares. You need to install the anti-virus software and set up firewalls and keep them updated.
Denial-Of-Service Attacks
The hackers render the site inaccessible to legitimate customers by overwhelming it with traffic and data until the website crashes. These attacks do not have a direct financial cost to the victims but the indirect cost of lost sales can be high along with the frustration of getting the website up and running again.
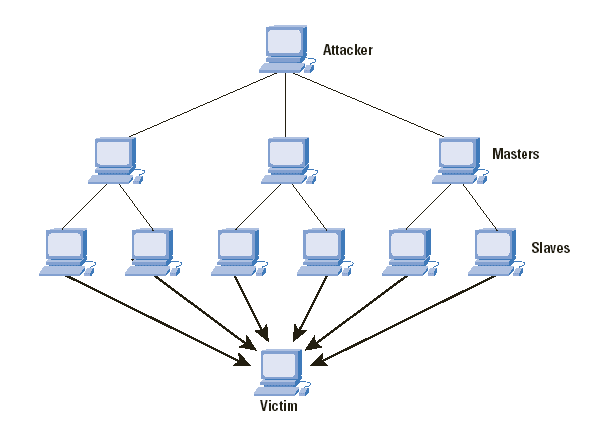
E-commerce websites, different types of high-profile businesses including media agencies and government organizations are more prone to these attacks. They need to keep their anti-virus software and security patches up-to-date and monitor traffic reports.
Man-In-The-Middle Attacks
The normal flow of data is from users to the servers and back. When there is a man-in-the-middle attack, the flow gets disrupted because the hacker intercepts the data being sent. The users are not even aware of what is happening or that their data has been breached.
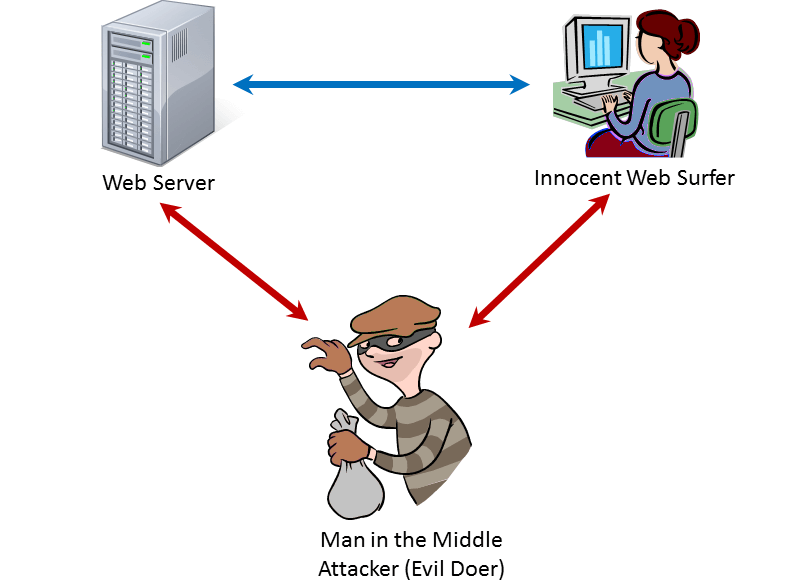
Always use a secured website. Enter only the confidential information on websites where the URL is “HTTPS” instead of HTTP. Pay attention if the browser warns that a website’s security certificate is out-of-date.
Eavesdropping Attack

The hackers listen in on data that flows through the network and get access to passwords, identifying details and credit card numbers. Eavesdropping attacks are harder to detect than man-in-the-middle attacks because the data still directly reaches its destination. In order to protect yourself, make sure that you use the data encryption in transit.
Drive-By Download Attacks

These are done to spread malware. The malicious code is uploaded to unsecured websites. When these sites are visited, the web server code automatically installs the malware or redirects the user to another corrupted site. These attacks may be lurking in emails or pop-up windows as well. Stay away from suspicious websites and keep your firewall software up to date. Also keep apps and plugins on your device to a minimum.
Final Thoughts
Staying vigilant towards cyber-attacks is the only way you can keep yourself safe. Businesses need to educate their employees and maintain the quality of anti-virus software and firewalls (Do not forget to update them).



